
Penetration Testing
Penetration testing services are the most comprehensive way for you to identify and mitigate risks in your cyber security.
It’s a simulated cyber-attack on your IT defences, just like a real cyber criminal would do. Penetration testing services help you to uncover and understand the weaknesses in your cyber security defences, so you have clarity on what steps to take to protect your business assets.
CyberUnlocked assists businesses and Managed Service Providers to build robust cyber security defences and protect their assets. Contact our team for a tailored programme to deep-dive into the strength of your cyber security.

Our Penetration Testing Services
At CyberUnlocked, our expert penetration testing services help you stay one step ahead of cyber threats
Common FAQs on
Penetration Testing
What are the types of penetration testing?
At CyberUnlocked, we offer a full-spectrum suite of penetration testing services designed to uncover your blind spots before attackers do. Here’s a breakdown of the key types:
External Penetration Testing: Fortify your perimeter. This test simulates real-world attacks from outside your network to identify and exploit vulnerabilities in internet-facing assets, like websites, firewalls, and email servers.
Internal Penetration Testing: Think like an insider threat. We assess your internal network to uncover risks that a malicious employee or an attacker with internal access could exploit, from privilege escalation to lateral movement.
Web Application and API Security Penetration Testing: Your web apps are prime targets. We pinpoint weaknesses in your websites and APIs, ensuring secure coding, session management, authentication, and data protection, all tailored to your tech stack.
Cloud Security Penetration Testing: Cloud environments need cloud-native defences. We identify misconfigurations, insecure interfaces, and access control flaws across AWS, Azure, GCP and more, keeping your workloads safe.
OT/SCADA and IoT Penetration Testing: Industrial and smart tech requires specialised attention. We simulate attacks on Operational Technology (OT), SCADA systems, and IoT networks, without disrupting critical processes, to highlight unique vulnerabilities.
Wireless Penetration Testing: Your wireless networks can be a threat vector. We test Wi-Fi networks to detect rogue access points, misconfigurations, and weak encryption.
Social Engineering Penetration Testing: Sometimes, the weakest link is human. We mimic phishing, vishing, and other social engineering tactics to assess how well your staff can identify and respond to psychological attack methods.
Physical Penetration Testing: Locks and cameras aren't always enough. We test your physical premises, access control systems, security personnel, and surveillance setups, to evaluate how well your organisation can withstand a physical intrusion.
What are the stages of penetration testing?
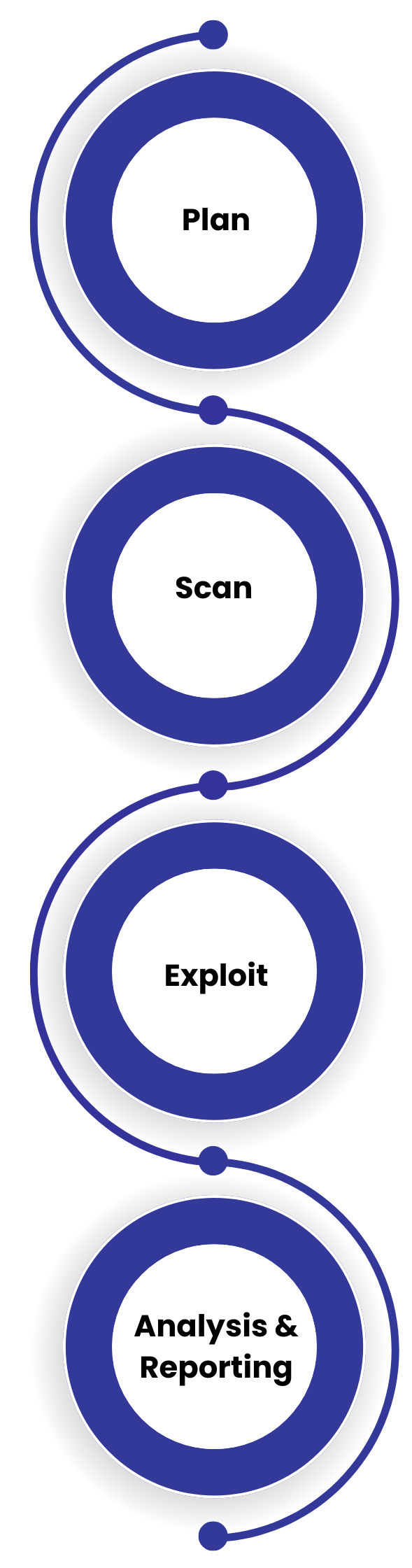
There are 4 stages of penetration testing in Australia
Plan: To design a test that will uncover as many weaknesses as possible and masquerade the abilities of the best cyber criminals.
Scan: Automated scans of the IT system, to uncover weaknesses.
Exploit: A manual step where a cyber security team exploits the weaknesses uncovered to gain unauthorised access. The goal is to enter as deep into the IT network as possible.
Analysis & Reporting: The team provides a report detailing its findings - including which tools cyber criminals could use to penetrate the IT system, a list of identified vulnerabilities, their level of risk, and recommendations to prevent future cyber-attacks.
What are the differences between vulnerability testing and penetration testing?
Vulnerability testing and penetration testing are two types of security risk assessment frameworks.
Vulnerability scanning is an automated scan that systemically analyses the security of an IT system, looking for weaknesses.
However, a penetration test is a simulated cyber-attack, manually carried out by cyber security experts. It is a more thorough test that emulates the savvy and ingenuity of how real cyber criminals attempt to hack into IT systems.
The difference is that vulnerability testing uncovers known weaknesses to protect against, while penetration testing is more comprehensive and tailored to the cyber risks a business may face.
How do I choose a penetration test vendor?
Cyber security is an arms race between white-hat and black-hat hackers. Successful penetration testing depends on having a team who can simulate the technical competence and creativity of cyber criminals in the real world, to make sure your business stays one step ahead.
Penetration testers should have experience and expertise in the area of specialisation. As your security consultant, they should always offer manual testing, to identify any false positives that an automated scan may pick up.
They should provide detailed documentation on the scope and rules of engagement before commencing, and provide a comprehensive report with the results.
How much does penetration testing cost, and what affects the price?
As no two systems are alike, we tailor every quote based on your environment. That said, most of our engagements range between $3,000 and $15,000 AUD, depending on scope, complexity, and compliance requirements.
Key factors that influence pricing:
• Number of assets (e.g. websites, servers, endpoints)
• Testing type (external, internal, web app, API, OT/IoT)
• Compliance standards (e.g. ISO 27001, SOCI Act etc)
Need a quick estimate? Book a 15-min discovery call. No sales fluff, just straight answers.
How soon can you start a penetration test?
We can usually kick off within 5–10 business days, depending on urgency and scope. If you're facing a tight compliance deadline or a product launch, let us know, and we’ll do our best to prioritise.
What industries have you worked with?
We’ve helped secure:
• Healthcare providers (where patient data is critical)
• SaaS and tech organisations
• Critical infrastructure and OT/SCADA environments
• Government agencies with strict compliance standards
• … and many others
Whether you’re running cloud-native platforms or legacy OT systems, we’ve likely seen it, and probably broken into it (ethically, of course).
What kind of report will I receive, and how detailed is it?
You’ll receive a clear, executive-ready report with:
• A prioritised list of findings
• Screenshots, evidence, and technical detail
• Business impact explanations
• Remediation guidance written in plain English
• A debrief session
No jargon. Just real insights you can act on immediately.
Will this impact my live systems or cause downtime?
Short answer: No. Our testing is carefully planned to avoid disruption.
We perform testing during agreed windows, use non-intrusive techniques where needed, and always communicate any high-risk actions in advance. Your uptime is safe with us.
Is this just automated scanning, or do you include manual testing?
Great question and a big difference.
We combine industry-grade automated tools with expert manual testing. That’s where the real value is. The automated tools miss logic flaws, chained exploits, and contextual vulnerabilities.
All our testers are humans, not just button-pushers.
Do you help us fix the vulnerabilities after testing?
Absolutely. We don’t just drop a report and disappear.
We provide:
• Remediation walkthroughs
• Fix verification (we can retest once you patch)
• Strategic advice to strengthen your security posture
Need more help? We also offer hands-on remediation support via our trusted partner network.
Can I choose between internal and external testing?
You sure can. We offer:
• External penetration testing: from the perspective of an internet-based attacker
• Internal penetration testing: assuming a breach or insider threat
• Hybrid packages that simulate real-world attack paths
Not sure what you need? We’ll recommend the right mix for your risk profile.
How often should we do penetration testing?
At a minimum, once per year, or any time you:
• Launch new systems or apps
• Undergo significant infrastructure changes
• Need to meet compliance milestones
• Experience a security incident
Proactive testing = fewer surprises (and fewer emergencies).


